Quick Links
Blockchain technology stores data in encrypted format in blocks. They are linked with previous blocks forming a chain of data known as blockchain. Each block contains a timestamp, a cryptographic hash of the previous block, and a set of transactions.
The fascinating fact about blockchain is that the chain operates in a decentralized nature where there is no central authority controlling but is guarded by a number of nodes (computers) each with a copy of the blockchain. Once a transaction is executed, the validators are required to validate it and reach a consensus to record it on the blockchain. Although decentralization offers several advantages, the system has its inherent drawbacks as occasional block conflicts may ensue.
Chain Reorganization
When two or more blocks are validated by miners simultaneously at the same block height, it causes a block conflict as the network splits into two or more paths resulting in multiple versions of the network. It may also occur when a user maliciously attacks the network and creates a longer chain than the main one or when the network introduces a fork which is not fully rolled out to all nodes in the network. Such occurrences are common in busier blockchains like Bitcoin and Ethereum and are known as chain reorganization or reorg.
How is Chain Reorganization Resolved ?
When the network splits in two or more different paths, and users continue to make transactions, new blocks are continuously added to each of the chains which leads to a disagreement on which version should be considered as the canonical chain.
In a PoW based blockchain, such a conflict is resolved by the ‘Longest Chain Rule’ and the chain with maximum blocks is considered valid as the longer chain represents the maximum computational work done behind it. The blocks in other shorter versions of the chain are deactivated & deleted and are then added in the longer chain.
Whereas, in a PoS based blockchain such as ethereum, block conflicts are resolved by fork choice algorithm which picks the block with maximum weight which is measured by the sum of validator votes scaled by their staked ETH balance. This process ensures that all nodes have the same copy of the blockchain.
How does a Chain Reorganization work?
I’ll take an example of a recent chain reorg that happened in Ethereum in 2022, few months before its transition to a complete PoS mechanism i.e the Ethereum Merge. The Beacon Chain, which introduced PoS to its ecosystem, experienced a seven block chain reorg from blocks 3,887,075 to 3,887,081.
The reorg was reported by Martin Koppemann, CoFounder of Gnosis (Ethereum sidechain) in a tweet on May 25,2022.
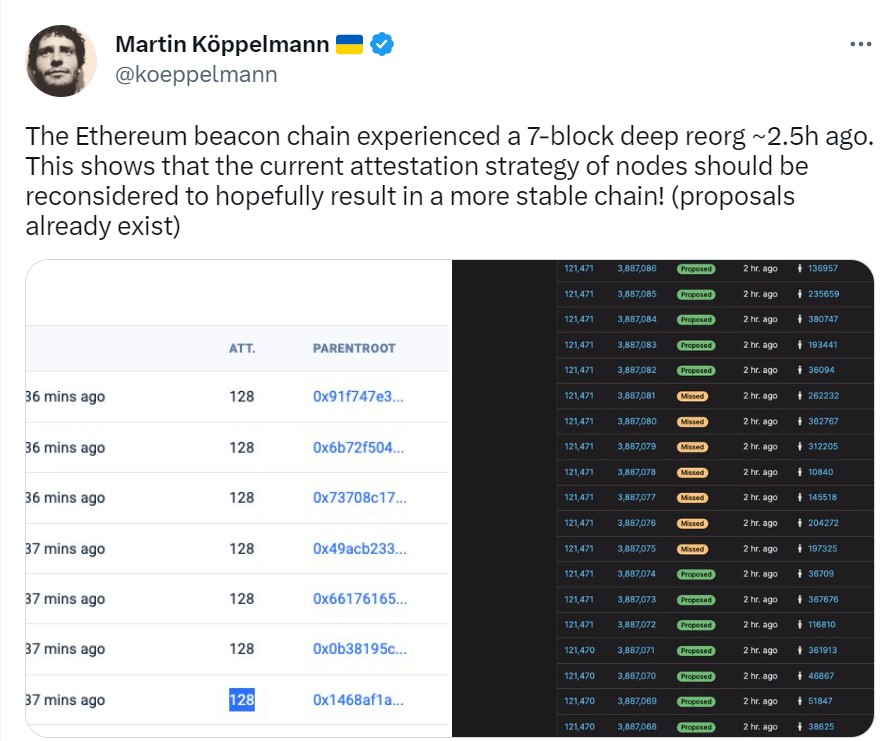
As everyone was speculating if it was an attack or a network issue, it was soon confirmed by Ethereum Developer, Preston Vanloon that the issue was caused by the implementation of a Proposer Boost fork choice that has not been received by all the nodes in the network. Consequently, the up-to- date nodes were faster than others who were at block 3,887,074 and seven blocks of transactions were added to the eventually discarded version of the chain until the network figured it wasn’t the primary chain.
Impact of Chain Reorganization
Regardless of the cause of chain reorganization, it may have a significant impact on the chain and its users.
(I) Double spending: A user may spend the same cryptocurrency twice causing huge losses for merchants accepting payments in cryptocurrency.
(II) Increase in Node Costs: The transactions which are a part of deleted or orphan blocks are invalidated and may take some time and additional cost to be verified and added again to the main chain. As a consequence, users may lose trust in the security which leads to a decrease in user adoption.
(III) 51% attacks: The system can also be vulnerable to 51% attacks when the attackers have enough computing power to create a chain greater than the primary chain. Misusing the controlling power, attackers can approve fraudulent transactions and double spend cryptocurrency. This can cause large financial losses to the users who accept payments on the network.
Conclusion
No consensus mechanism is foolproof and both PoW & PoS are vulnerable to chain reorganization. PoW is more prone to 51% attacks as a miner can control maximum computing power of the network, however in the case of PoS, owning more than 50% of the network’s stake is difficult to achieve. However, reorg in PoS includes the scope of double spending and losses for its users. Both mechanisms have their own advantages and disadvantages and it is important for network participants to remain vigilant and monitor the network for potential attacks.













