Quick Links
In the ever-changing realm of cryptocurrencies, where privacy and security are essential, ground-breaking innovations, and lucrative prospects flourish, a disturbing reality is hidden beneath the glimmering surface – crypto scams or hacks. With the tremendous growth and global fascination surrounding digital currencies, it is no surprise that the risk of fraudulent schemes has also risen.
Tornado Cash which emerged as a leading decentralized mixer, providing users with a way to protect their transaction history and maintain their anonymity, fell prey to a significant attack, exacerbating the challenges faced by this popular protocol on May 20 at 7:25 UTC when an attacker cunningly exploited Tornado Cash’s governance system, wielding it as a potent weapon to seize complete control. In this blog post, we will learn more about Tornado Cash and its working, followed by the details of this attack and its aftermath!
What is Tornado Cash?
Tornado Cash is an open-source, fully decentralized, non-custodial cryptocurrency tumbler that runs on networks compatible with the Ethereum Virtual Machine. It offers a service that mixes possibly traceable or “tainted” cryptocurrency funds with others, making it harder to find where the money came from in the first place. This is a privacy tool for EVM networks, where all activities are public by default. Here are some of the characteristics of the coin mixer:
- Decentralized: The code for Tornado Cash is open source, and a DAO runs its operations. This source code was posted on GitHub until the main repository was removed after OFAC’s statement.
- Non-custodial: Tornado Cash never takes control of its users’ money during the mixing process.
- Smart contract: Tornado Cash is a code that runs on public blockchains like Ethereum. Most of its smart contracts are made in a way that makes it impossible for anyone, even the Tornado Cash DAO, to change or destroy them.
The Process of Mixing Funds
1) The user makes a “deposit note” on their device and sends an encryption hash to their chosen Tornado Cash pool contract.
2) The user then sends money to the contract, which pools this deposit with deposits from other users in amounts set by the contract, such as 0.1, 10, or 50 ETH.
3) After this, the user utilizes their secret deposit note and zero-knowledge cryptography to make a transaction that shows they have the right to withdraw the value they deposited.
Controversial History of Tornado Cash
On August 8, 2022, Tornado Cash was blacklisted by the U.S. Department of the Treasury’s Office of Foreign Assets Control. This decision rendered it unlawful for individuals, residents, and businesses in the United States to send or receive money through the service. The Treasury Department accused Tornado Cash of facilitating the movement of over $7 billion in virtual currencies, including $455 million believed to have been stolen in 2022 by the Lazarus Group, a hacking organization linked to the North Korean government.
Circle, the company behind USD Coin, froze about $75,000 in USDC from Ethereum addresses that belonged to the dealer. Alexey Pertsev, who made Tornado Cash, was arrested in Amsterdam on August 10, 2022, on suspicion of “helping hide criminal financial flows and launder money by mixing cryptocurrencies through the decentralized Ethereum mixing service Tornado Cash.” After this, a cryptography professor at Johns Hopkins re-uploaded the code in the name of free speech.
Latest Attack on Tornado Cash
At 7:25 UTC on May 20, an attacker executed a cunning maneuver, effectively granting 1.2 million votes upon a malicious proposal. Considering the proposal had already garnered over 700,000 genuine votes, the attacker seamlessly secured absolute control over the governance of Tornado Cash.
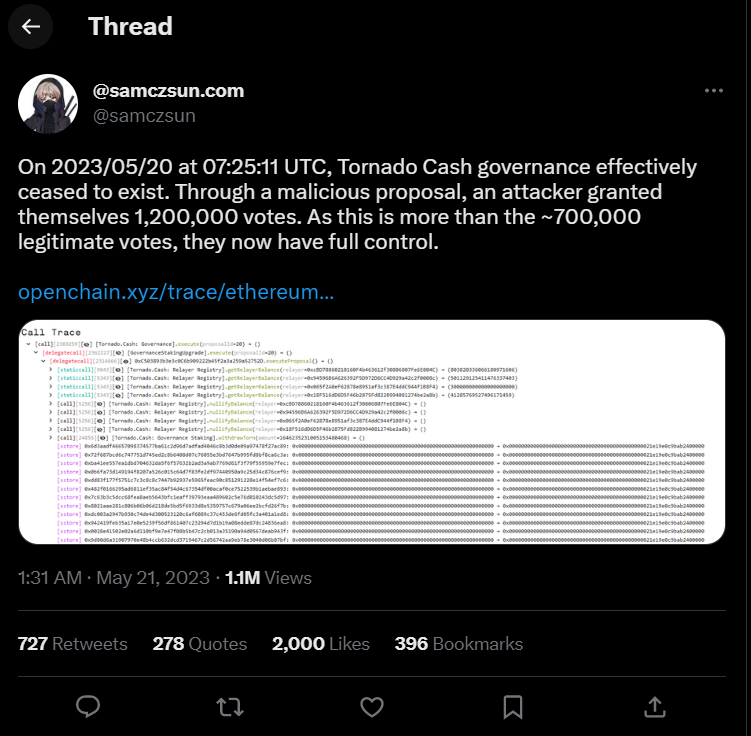
At 7:25 UTC on May 20, an attacker executed a cunning maneuver, effectively granting 1.2 million votes upon a malicious proposal. Considering the proposal had already garnered over 700,000 genuine votes, the attacker seamlessly secured absolute control over the governance of Tornado Cash.
@samczsun, a prominent figure from Paradigm, a research-driven technology investment firm, shared crucial information regarding the malicious proposal targeting Tornado Cash. “In their announcement, the attacker claimed to have utilized a logic resembling a previously approved proposal by the community. However, this time, the proposal included an additional function.”
With complete control over Tornado Cash governance, the attacker possesses the capability to withdraw all locked votes, deplete tokens within the governance contract, and render the router inoperable. At present, the attacker has already started 10,000 votes in TORN and subsequently sold them.
This attack is a stark reminder for crypto investors to evaluate proposal descriptions and underlying logic meticulously. Tornadosaurus-Hex, an active member of the Tornado Cash community, has acknowledged that all funds held in governance are potentially compromised. Consequently, they have urged all members to withdraw their locked funds.
Furthermore, attempts have been made to deploy a contract that could reverse the changes while encouraging community members to retrieve their funds. The Tornado Cash community of developers has expressed the urgent need for Solidity developers and are trying to get in touch with Binance, as the exchange holds more tokens than the attacker. Their hope lies in finding a solution that empowers the community to safeguard against hackers exploiting the anonymity of honest users without excessive regulations or compromising the principles of the crypto ecosystem.
How did the attacker execute this attack?
On May 13, 2023, at 7:07 (UTC), the exploiters created the proposal contract 0xC503893b3e3c0C6b909222b45f2a3a259a52752D through the contract 0xAF54612427d97489707332efe0b6290F129DbAcb.
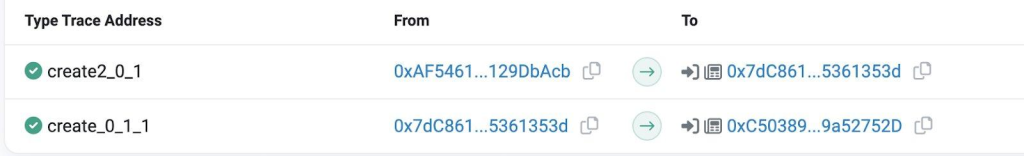
On May 13, 2023, AT 7:22 (UTC), the exploiters initiated the #20 proposal, presenting it as an extension to the #16 proposal with similar execution logic.
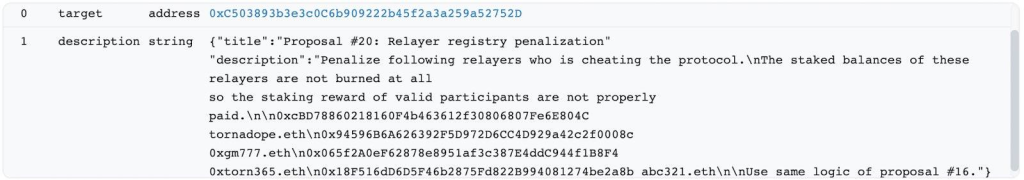
However, the proposal contract contained additional self-destruct logic. The creator of this contract, 0x7dC86183274b28E9f1a100a0152DAc975361353d, used the create2 function to generate it and included a self-destruct function. This allowed the exploiters to destroy the proposal contract and redeploy different bytecodes to the same address.
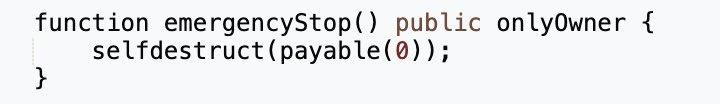
Unfortunately, the community did not detect the presence of malicious intent in the proposed contract, leading many users to vote in favor of it. Exploiting the ability to destroy and redeploy the proposal contract with altered logic, the exploiters dismantled the execution contract and deployed a malicious contract in its place. This new contract was designed to modify the number of tokens locked by users in governance.
On May 18, 2023, between 8:49 to 9:01 UTC, exploiters repeatedly locked 0 tokens in governance by creating new addresses with multiple transactions. Once the exploiters finished manipulating the proposal contract, they executed the malicious proposal at 7:25 (UTC) on May 20, 2023. The execution occurred via Delegatecall, modifying the token lock amount to 10,000 for addresses controlled by the exploiters within the governance contract. Following the proposal’s execution, the exploiters unlocked TORN tokens from the Governance Vault, depleting its reserve and gaining control over governance.
Aftermath of the Attack
Following the attack on the DAO, the Tornado Cash token (TORN) has experienced a 10% surge in value, which comes in response to a proposal submitted by a wallet address associated with the attack, which aims to reverse the malicious alterations made.
A few hours after the hack, the attacker contacted the Tornado Cash community with an unexpected proposal, indicating their intention to return governance control. In the Tornado Cash community forum, user Tornadosaurus-Hex shared the news, mentioning the attacker’s new proposal to restore the governance state. Hex believed there was a “good chance” the attacker would follow through with the proposal.
According to Tornadosaurus-Hex, the attacker is relinquishing the TORN tokens they had granted themselves, which had given them significant control over governance votes, reducing their share back to zero. Hex further assured the community that diligent verification of storage layouts had occurred, indicating compliance with the attacker’s chosen method of returning governance control.
Considering the attacker’s substantial holdings of TORN governance tokens, the proposal will likely pass as voting concludes on May 26, although the exact execution timeline remains unclear. Once the proposal is approved, the malicious code integrated into the protocol, which enabled the theft of voting power from others, will be removed, and the governance of Tornado Cash’s DAO will revert to token holders. While some community members express optimism regarding the attacker’s apparent change of heart, others speculate that it may be an attempt to artificially boost the price of the TORN token before ultimately cashing out.
Conclusion
To conclude, Tornado Cash aims to provide users privacy and security in the fast-paced world of cryptocurrencies. However, the recent attack on Tornado Cash’s governance system has exposed vulnerabilities and posed significant challenges to the protocol. This attack reminds crypto investors about the importance of carefully evaluating proposal descriptions and underlying logic.
As the voting on the latest proposal continues, the outcome remains uncertain. If approved, the malicious code will be removed, and Tornado Cash’s DAO governance will be restored to token holders. The aftermath of this attack highlights the resilience and collaborative efforts of the crypto community in safeguarding against exploitation and striving for a secure and decentralized future.









